Modeling Attacks on AI-Powered Apps with the AI Kill Chain Framework
Sources: https://developer.nvidia.com/blog/modeling-attacks-on-ai-powered-apps-with-the-ai-kill-chain-framework, https://developer.nvidia.com/blog/modeling-attacks-on-ai-powered-apps-with-the-ai-kill-chain-framework/, NVIDIA Dev Blog
TL;DR
- The AI Kill Chain defines five stages—recon, poison, hijack, persist, and impact—with an iterate/pivot branch to model attacker progression against AI-powered apps.
- Recon focuses on mapping the system and observing errors and behavior; disrupting recon early is a defensive priority.
- Poison targets model inputs; text-based prompt infection is the most common technique, with other methods noted but not exhaustively enumerated in the public write‑up.
- Hijack is the active manipulation of model behavior, with heightened risk in agentic workflows where goals, not just outputs, can be steered autonomously.
- Persist, iterate/pivot, and impact describe how attackers gain ongoing control, escalate their foothold, and drive real-world effects via downstream tools and actions.
Context and background
AI-powered applications introduce new attack surfaces that traditional security models do not fully capture, particularly as agentic systems gain autonomy. The AI Kill Chain builds on the Cyber Kill Chain concept by focusing on attacks against AI systems themselves rather than attackers using AI. NVIDIA’s framework is designed to illustrate where defenders can break the chain and how to connect this model to other security approaches. The framework emphasizes stage-by-stage defenses and provides concrete examples to help security teams anticipate attacker behavior in AI-enabled environments. NVIDIA also notes that many defenses are operationalized through technologies such as NeMo Guardrails, Jailbreak Detection NIMs, and architectural best practices. For readers seeking deeper context, the NVIDIA blog discusses best practices for securing LLM-enabled applications and the framework for understanding agentic autonomy levels and security, along with their NVIDIA AI red team.
What’s new
The AI Kill Chain formalizes an attack lifecycle specifically for AI systems, outlining five core stages plus an iterate/pivot branch to account for feedback loops in agentic environments. The model helps security teams move beyond generic “prompt injection” concerns to identify precise points where attackers can gain control and extend their influence. The blog also uses a simple Retrieval-Augmented Generation (RAG) application as a concrete example to show how an exfiltration scenario might unfold and how defenses could interrupt the chain at each stage. This approach underscores that securing AI requires layered defenses that scale with autonomy levels and that the attack surface evolves as enterprises deploy LLMs, RAG systems, and agentic workflows.
Why it matters (impact for developers/enterprises)
- Attacks on AI systems can cascade beyond the model itself, affecting downstream tools, APIs, and workflows that execute real-world actions. The framework highlights that security must extend to how model outputs are used and invoked downstream.
- Agentic systems—where models plan, decide, and act autonomously—pose specific risks at the hijack and iterate/pivot stages, where attackers can steer goals and automate malicious actions across sessions.
- By breaking the AI Kill Chain at different stages, organizations can disrupt attacker progress early (recon), prevent manipulation of inputs (poison), prevent functional control (hijack), and limit long-term presence (persist and iterate/pivot).
- NVIDIA points to practical defenses such as NeMo Guardrails, Jailbreak Detection NIMs, and architectural best practices as part of an integrated security strategy for AI-enabled applications.
Technical details or Implementation
The AI Kill Chain comprises five stages and an iterate/pivot branch:
- Recon: Attacker maps the system, probes behavior and errors, and gathers observability to tailor subsequent steps. Defensive priority: disrupt recon early to prevent attackers from gaining the knowledge they need.
- Poison: The attacker places malicious inputs so they will be processed by the AI model. The most common technique is text-based prompt infection; other techniques are acknowledged but not exhaustively enumerated in the public write‑up. Defensive priority: interrupting inputs and signals that seed malicious behavior.
- Hijack: Malicious inputs are ingested and steer the model toward attacker objectives. In agentic workflows, hijack can be more powerful because it can influence goals, not only outputs. Defensive priority: breaking the chain at hijack protects downstream systems even if poisoning occurred.
- Persist: Attackers embed malicious payloads into persistent storage to maintain influence across sessions. Defensive priority: prevent permanent footholds and recurrent exploitation from hijacked states.
- Iterate/Pivot: In agentic systems, attackers can continually refine, adapt, and escalate their control through a feedback loop, turning a single hijack into broad compromise. Defensive priority: interrupt this loop to prevent progressive, systemic exploitation.
- Impact: The attacker’s objectives materialize when hijacked outputs trigger actions that affect systems, data, or users beyond the model itself. Defensive priority: implement robust downstream controls on tool invocation and data flows to contain attacker reach. Table: AI Kill Chain stages and defensive priorities | Stage | What the attacker tries to achieve | Defensive priority |--- |--- |--- | Recon | Map the system and observe behavior to guide the attack | Disrupt reconnaissance to limit attacker knowledge | Poison | Introduce malicious inputs as the model processes data | Break the poisoning attempt by restricting input channels | Hijack | Ingest and steer model behavior toward attacker goals | Break at hijack to protect downstream systems | Persist | Establish ongoing control across sessions | Prevent persistent footholds and recurrent exploitation | Iterate/Pivot | Evolve attacker control via feedback loops | Interrupt iteration to prevent systemic compromise | Impact | Trigger real-world actions via downstream tools | Control tool invocation and data flows to limit impact
Key takeaways
- The AI Kill Chain provides a structured lens to analyze attacks against AI-powered apps, emphasizing stages where defenses can intervene.
- Agentic autonomy elevates risk at hijack and iterate/pivot stages, underscoring the need for controls beyond the model itself.
- Defensive strategies must be layered, spanning from input validation and prompt safety to downstream tool controls and data-flow governance.
- NVIDIA’s approach highlights practical implementations and ongoing research efforts (e.g., NeMo Guardrails, Jailbreak Detection NIMs) as part of a broader security program.
- The framework supports organizations in moving from generic prompt-injection concerns to actionable, stage-by-stage defense planning.
FAQ
-
What is the AI Kill Chain?
It is a framework that models how attackers compromise AI-powered applications, outlining stages from reconnaissance to impact and including an iterate/pivot branch to reflect feedback loops in agentic systems.
-
How does the AI Kill Chain differ from traditional Cyber Kill Chain concepts?
It focuses specifically on attacks against AI systems themselves rather than attackers using AI, providing stage-based defensive priorities tailored to AI-enabled workflows.
-
What are the main stages, and why are they important for security teams?
The stages are recon, poison, hijack, persist, and impact, with an iterate/pivot branch. Each stage identifies where defenses can interrupt attacker progression and reduce risk of downstream impact.
-
How can organizations apply these ideas in practice?
By mapping AI-enabled applications to the AI Kill Chain, prioritizing protections at each stage, and implementing downstream controls for tool invocation and data flows, as part of an overall security strategy.
-
What role do NVIDIA technologies play in these defenses?
NVIDIA references technologies like NeMo Guardrails, Jailbreak Detection NIMs, and architectural best practices as part of operationalizing these defenses in real-world AI deployments.
References
More news
NVIDIA HGX B200 Reduces Embodied Carbon Emissions Intensity
NVIDIA HGX B200 lowers embodied carbon intensity by 24% vs. HGX H100, while delivering higher AI performance and energy efficiency. This article reviews the PCF-backed improvements, new hardware features, and implications for developers and enterprises.
Shadow Leak shows how ChatGPT agents can exfiltrate Gmail data via prompt injection
Security researchers demonstrated a prompt-injection attack called Shadow Leak that leveraged ChatGPT’s Deep Research to covertly extract data from a Gmail inbox. OpenAI patched the flaw; the case highlights risks of agentic AI.
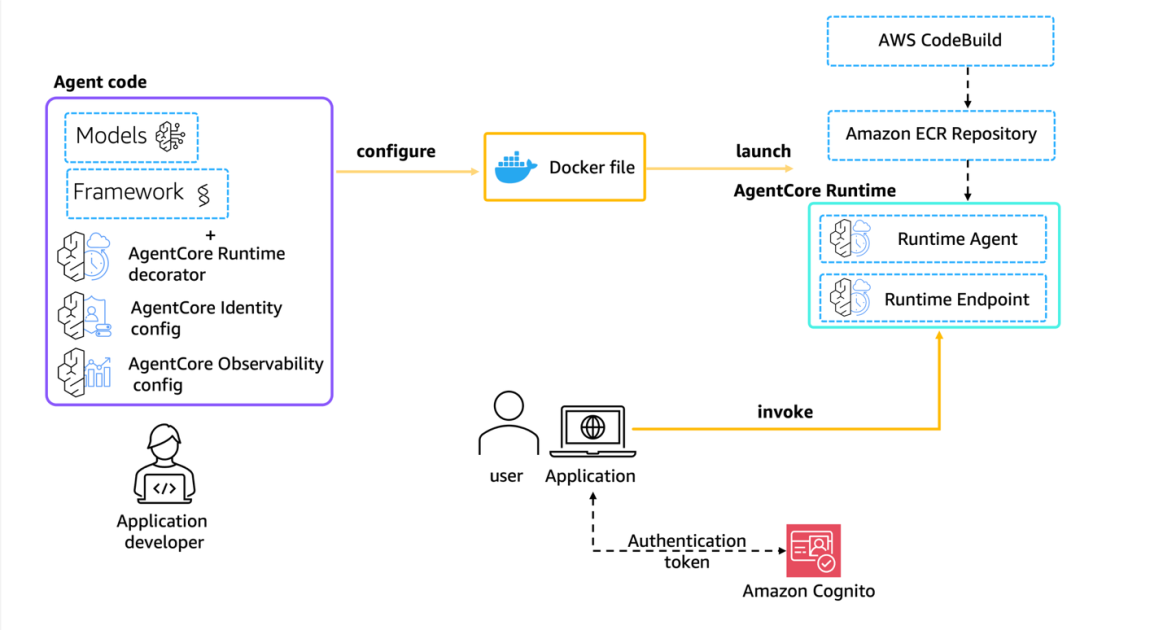
Move AI agents from proof of concept to production with Amazon Bedrock AgentCore
A detailed look at how Amazon Bedrock AgentCore helps transition agent-based AI applications from experimental proof of concept to enterprise-grade production systems, preserving security, memory, observability, and scalable tool management.
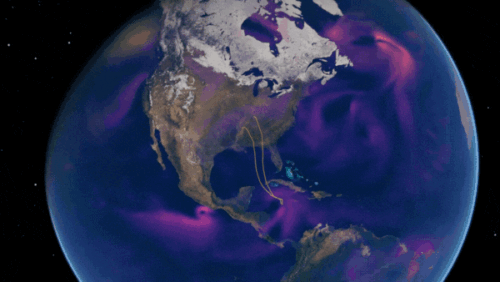
Predict Extreme Weather in Minutes Without a Supercomputer: Huge Ensembles (HENS)
NVIDIA and Berkeley Lab unveil Huge Ensembles (HENS), an open-source AI tool that forecasts low-likelihood, high-impact weather events using 27,000 years of data, with ready-to-run options.
How to Reduce KV Cache Bottlenecks with NVIDIA Dynamo
NVIDIA Dynamo offloads KV Cache from GPU memory to cost-efficient storage, enabling longer context windows, higher concurrency, and lower inference costs for large-scale LLMs and generative AI workloads.
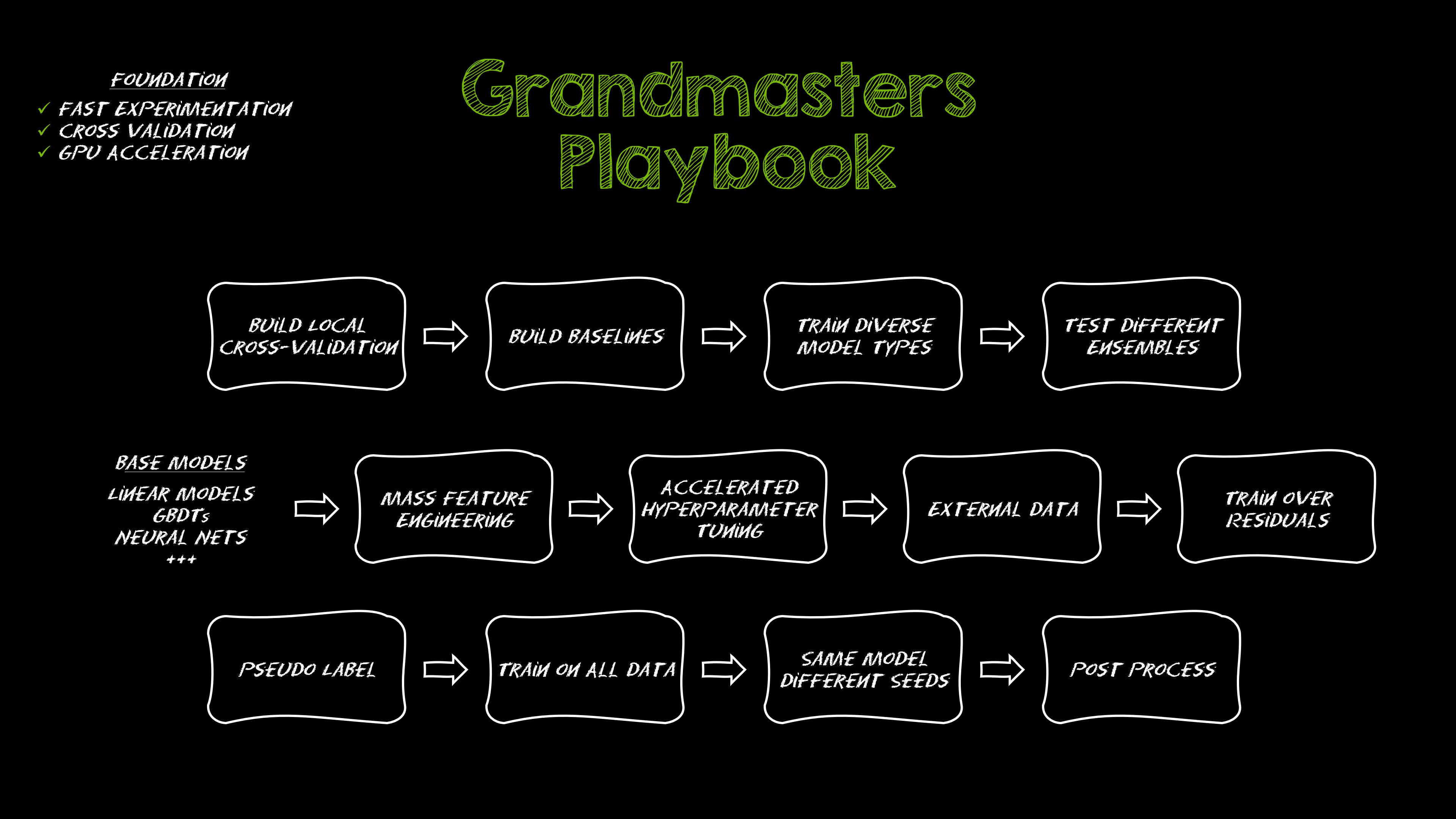
Kaggle Grandmasters Playbook: 7 Battle-Tested Techniques for Tabular Data Modeling
A detailed look at seven battle-tested techniques used by Kaggle Grandmasters to solve large tabular datasets fast with GPU acceleration, from diversified baselines to advanced ensembling and pseudo-labeling.