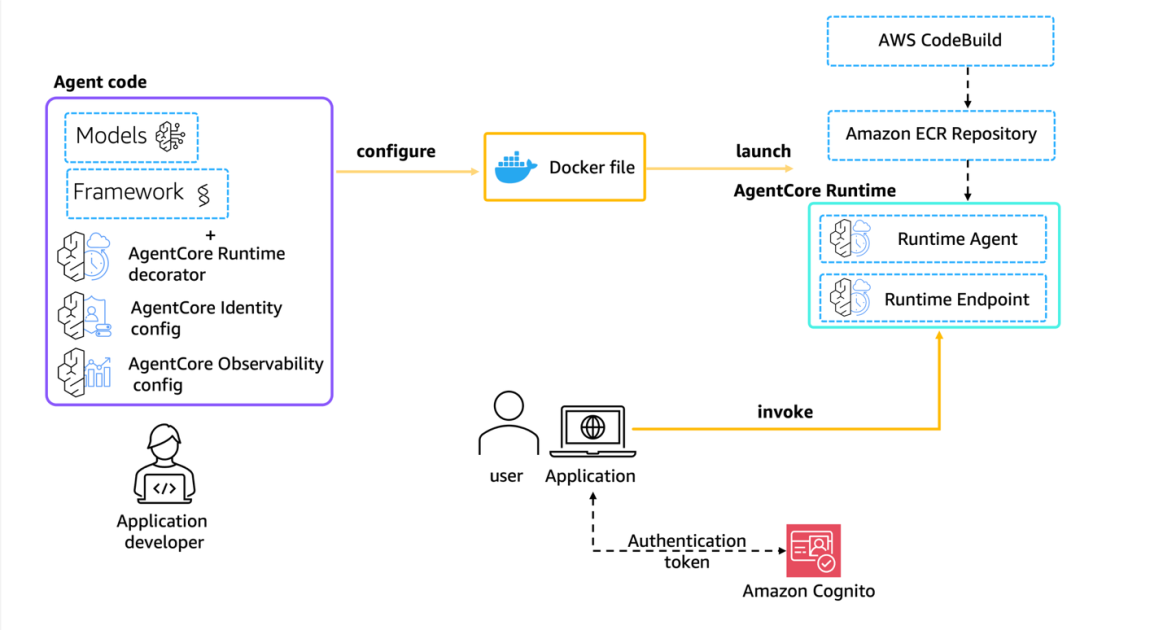
Set up custom domain names for Amazon Bedrock AgentCore Runtime agents
Sources: https://aws.amazon.com/blogs/machine-learning/set-up-custom-domain-names-for-amazon-bedrock-agentcore-runtime-agents, https://aws.amazon.com/blogs/machine-learning/set-up-custom-domain-names-for-amazon-bedrock-agentcore-runtime-agents/, AWS ML Blog
TL;DR
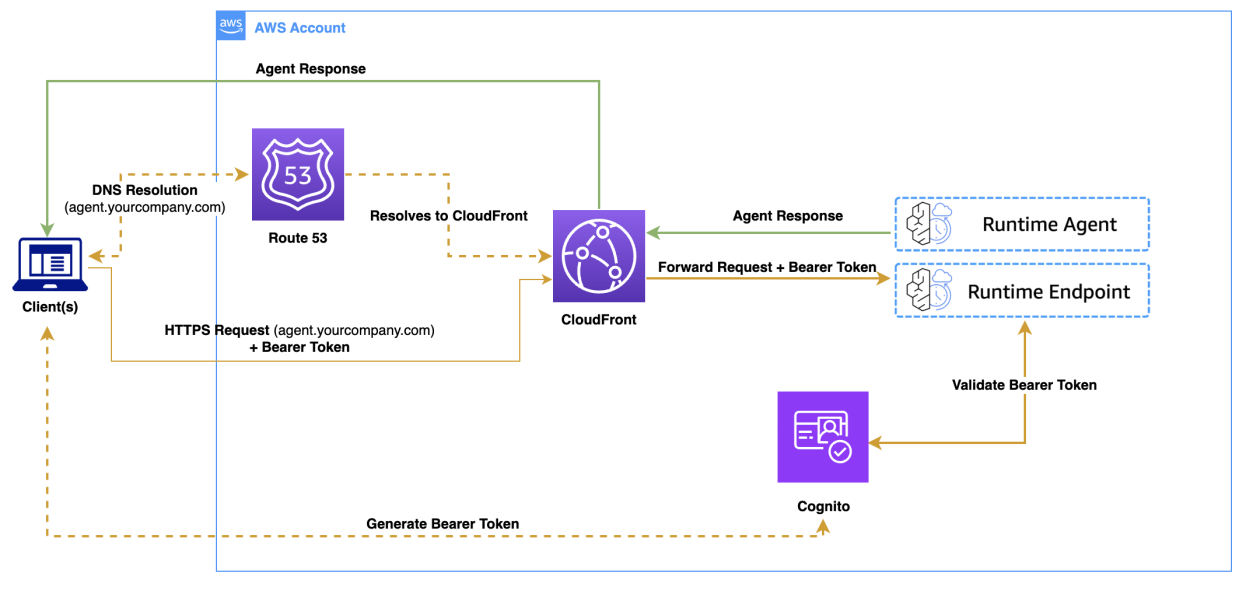
- Use CloudFront as a reverse proxy to map a custom domain, such as https://agent.yourcompany.com, to Amazon Bedrock AgentCore Runtime endpoints.
- Combine CloudFront, Amazon Route 53, and AWS Certificate Manager (ACM) to create a secure, scalable custom-domain setup that works with existing agents.
- Benefits include simplified integration for development teams, custom domains aligned with your organization, and cleaner infrastructure abstraction that helps with maintenance when endpoints update. You can serve both frontend and backend from the same domain to avoid CORS issues.
- The solution requires SSL certificates in the us-east-1 region (for CloudFront), and the deployment is implemented with the AWS CDK. It also presumes you may be using OAuth authentication with Amazon Cognito and that you have the agent runtime ARN handy after deployment.
- This approach is described in detail in the AWS ML Blog post, which also covers testing, cleanup, and considerations for production use.
Context and background
Amazon Bedrock AgentCore Runtime is described as a framework-agnostic hosting solution for AI agents. It supports agents built with LangGraph, CrewAI, Strands Agents, or custom implementations, and provides extended execution times up to 8 hours, isolated microVMs for each user session, and a consumption-based pricing model. The platform includes built-in authentication and specialized observability for AI agents. When using AgentCore Runtime with Open Authorization (OAuth), applications can communicate directly over HTTPS to the service endpoint. While this direct approach works, there are clear advantages to adopting a custom domain. By employing CloudFront as a reverse proxy, custom-domain traffic is transformed into Bedrock AgentCore Runtime API calls behind the scenes, allowing clients to reach a friendly URL such as https://agent.yourcompany.com/ without changing application logic. In addition to CloudFront, the solution relies on Route 53 for DNS management and ACM for SSL/TLS certificates. CloudFront SSL certificates must reside in the us-east-1 region, which is a known constraint for this approach. The original post also emphasizes that a single CloudFront distribution can be used to serve both frontend assets and backend agent endpoints, avoiding cross-origin resource sharing (CORS) issues because all content originates from the same domain. The AWS CDK is used to implement the custom-domain setup. A complete stack is provided in the post to create the CloudFront distribution that proxies custom-domain requests to the Bedrock AgentCore Runtime endpoints. If your frontend runs on a different domain than your agent endpoint, you will need to configure CORS headers so that requests from the frontend domain to the agent domain are allowed. You’ll also want to set caching policies to ensure agent responses stay dynamic (i.e., disable caching for agent responses). If you’re starting from scratch, you’ll create (or identify) the agent runtime ARN after deployment, as you’ll need it for the custom-domain configuration. The post also highlights a testing workflow using a JWT token from Amazon Cognito and shows how to test against both the custom domain and the default CloudFront domain.
What’s new
This approach documents how to leverage CloudFront as a reverse proxy to expose a custom-domain endpoint for Amazon Bedrock AgentCore Runtime agents. Key elements include:
- A CloudFront distribution configured to forward requests from your custom domain to the Bedrock AgentCore Runtime API calls.
- A single distribution that can serve both frontend and backend components, reducing CORS complexity.
- An AWS CDK-based implementation that packages CloudFront, Route 53, ACM, and the required permissions into a reusable stack.
- Clear guidance on prerequisites, such as ensuring SSL certificates exist in us-east-1 and obtaining the agent runtime ARN post-deployment.
- Testing instructions using Cognito-provided JWTs to authenticate with the custom domain or the CloudFront domain, and steps to verify successful agent responses.
Why it matters (impact for developers/enterprises)
- Simplified integration: Teams can point applications to a familiar domain rather than a technical Bedrock endpoint, streamlining onboarding and development workflows.
- Domain alignment with the organization: Custom domains support branding and consistency across applications and services.
- Cleaner infrastructure: By serving frontend and backend from a single domain, cross-origin issues are mitigated, reducing debugging effort and potential security concerns.
- Production readiness considerations: The approach emphasizes authentication, observability, and maintainability, and it notes the importance of resource cleanup to control ongoing costs.
- Security and scalability: The solution uses a reverse proxy setup with CloudFront, accelerated by ACM certificates, Route 53 DNS, and the Bedrock AgentCore Runtime’s built-in authentication and observability features.
Technical details or Implementation
The original article provides a detailed walkthrough of deploying a CloudFront-based reverse-proxy configuration for Bedrock AgentCore Runtime. Core considerations include:
- The default AgentCore Runtime endpoint resembles https://bedrock-agentcore.`{region}`.amazonaws.com/runtimes/`{EncodedAgentARN}`/invocations. The goal is to present a user-friendly custom domain such as https://agent.yourcompany.com.
- You must choose domain options provided in the walkthrough, and if you are testing quickly, you can start with a predefined option before configuring a full custom domain.
- SSL certificates for CloudFront must reside in us-east-1. This is a specific requirement of CloudFront when used with ACM for regional certificates.
- If your frontend domain differs from your agent domain, you should configure CORS headers so that requests from the frontend domain to the agent domain are allowed.
- To disable caching for agent responses and ensure dynamic content, set the CloudFront cache policy to CachePolicy.CACHING_DISABLED.
- The complete AWS CDK stack is provided in the post to orchestrate the CloudFront distribution, the Route 53 hosted zone (if applicable), and the ACM certificate, along with the necessary permissions to proxy requests to the Bedrock AgentCore Runtime endpoints.
- After deployment, you can test using the custom domain or the CloudFront default domain. Testing steps include obtaining a JWT token from Amazon Cognito and using it to call the agent endpoint. The post provides code samples for both the custom-domain URL and the CloudFront URL to validate proper responses.
- Cleanup guidance: To avoid ongoing costs, delete resources when no longer needed, including Route 53 hosted zones and ACM certificates. From a security and operations perspective, AgentCore Runtime offers built-in authentication and specialized observability for AI agents. The platform is designed to be used in conjunction with OAuth (Open Authorization) and Amazon Cognito as an identity provider when implementing the custom-domain approach. The integration enables developers to authenticate requests using tokens issued by Cognito and to verify that requests to the Bedrock endpoint flow through the CloudFront proxy. The post emphasizes that Amazon Bedrock AgentCore is currently in preview and subject to change. It also notes standard AWS pricing applies to additional services used (CloudFront, Route 53, ACM), meaning you should account for these costs in production planning.
Implementation outline (high level)
- Identify or deploy an AgentCore Runtime-based agent and capture its runtime ARN after deployment.
- Prepare a custom domain (e.g., agent.yourcompany.com) and configure DNS/SSL in us-east-1 through Route 53 and ACM.
- Deploy a CloudFront distribution using AWS CDK that forwards requests to the AgentCore Runtime endpoints, applying a non-cached policy for dynamic responses.
- If the frontend and agent endpoints share a domain, configure CORS to permit cross-domain requests as required.
- Test the setup by obtaining a Cognito JWT and issuing test requests to both the custom-domain endpoint and the CloudFront domain.
- Monitor and maintain security and observability features provided by AgentCore Runtime, and plan for resource cleanup when the environment is no longer needed.
Key takeaways
- Custom domains can simplify integration and align with organizational branding when using Bedrock AgentCore Runtime.
- CloudFront, Route 53, and ACM provide a cohesive stack to host a secure, scalable proxy in front of Bedrock AgentCore Runtime endpoints.
- A single CloudFront distribution can serve both frontend and backend components, reducing CORS complexity.
- Use the AWS CDK stack provided in the post to automate deployment and minimize manual steps.
- Plan for security, monitoring, and cost management, including resource cleanup after use.
FAQ
-
What is the benefit of using a custom domain with Bedrock AgentCore Runtime?
It provides a professional, seamless experience, aligns with organizational branding, and helps simplify integration by centralizing access under a single domain while preserving secure, direct API calls to the AgentCore Runtime.
-
Which AWS services are used in this solution?
The solution uses Amazon CloudFront as a reverse proxy, Amazon Route 53 for DNS, and AWS Certificate Manager (ACM) for SSL certificates, orchestrated via the AWS CDK.
-
Are there any prerequisites for SSL certificates and regions?
Yes. SSL certificates for CloudFront must be in the us-east-1 region. The post notes this requirement and explains how it fits into the overall architecture.
-
How do I test the custom-domain setup?
fter deployment, test using a JWT token from Amazon Cognito to authenticate requests to the custom domain or the CloudFront domain, validating that responses flow through the proxy to Bedrock AgentCore Runtime.
-
What should I do to clean up resources when the setup is no longer needed?
Delete the CloudFront distribution, ACM certificates, and any Route 53 hosted zones created for the solution to avoid ongoing costs.
References
More news
Move AI agents from proof of concept to production with Amazon Bedrock AgentCore
A detailed look at how Amazon Bedrock AgentCore helps transition agent-based AI applications from experimental proof of concept to enterprise-grade production systems, preserving security, memory, observability, and scalable tool management.
Prompting for precision with Stability AI Image Services in Amazon Bedrock
Amazon Bedrock now offers Stability AI Image Services, extending Stable Diffusion and Stable Image with nine tools for precise image creation and editing. Learn prompting best practices for enterprise use.
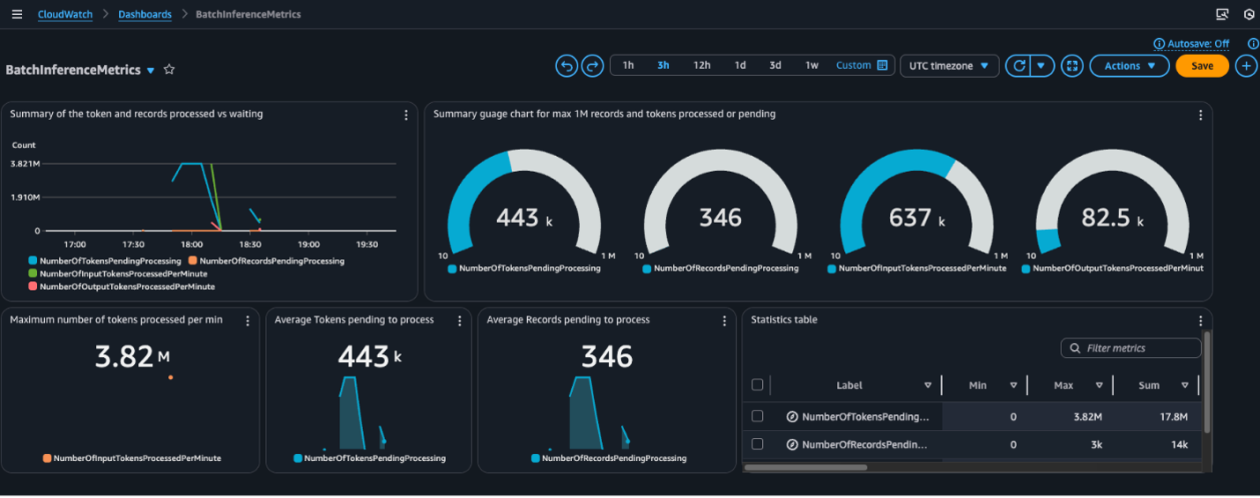
Monitor Amazon Bedrock batch inference using Amazon CloudWatch metrics
Learn how to monitor and optimize Amazon Bedrock batch inference jobs with CloudWatch metrics, alarms, and dashboards to improve performance, cost efficiency, and operational oversight.
Scale visual production using Stability AI Image Services in Amazon Bedrock
Stability AI Image Services are now available in Amazon Bedrock, delivering ready-to-use media editing via the Bedrock API and expanding on Stable Diffusion models already in Bedrock.
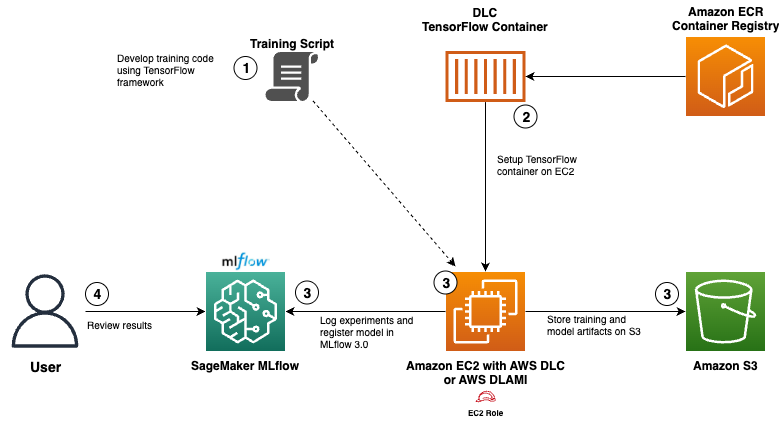
Use AWS Deep Learning Containers with Amazon SageMaker AI managed MLflow
Explore how AWS Deep Learning Containers (DLCs) integrate with SageMaker AI managed MLflow to balance infrastructure control and robust ML governance. A TensorFlow abalone age prediction workflow demonstrates end-to-end tracking, model governance, and deployment traceability.
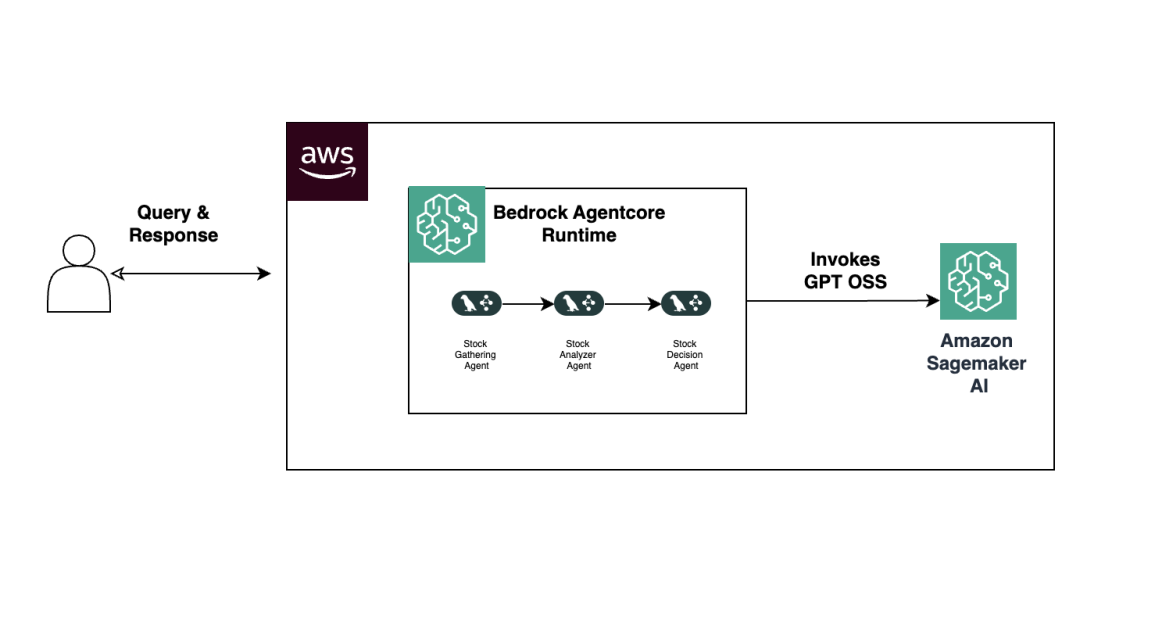
Build Agentic Workflows with OpenAI GPT OSS on SageMaker AI and Bedrock AgentCore
An end-to-end look at deploying OpenAI GPT OSS models on SageMaker AI and Bedrock AgentCore to power a multi-agent stock analyzer with LangGraph, including 4-bit MXFP4 quantization, serverless orchestration, and scalable inference.