Crescent library brings privacy to digital identity systems
Sources: https://www.microsoft.com/en-us/research/blog/crescent-library-brings-privacy-to-digital-identity-systems, https://www.microsoft.com/en-us/research/blog/crescent-library-brings-privacy-to-digital-identity-systems/, Microsoft Research
TL;DR
- Crescent library from Microsoft Research aims to improve privacy in digital identity systems. source
- It prevents tracking across uses and lets users disclose only what’s necessary from their credentials.
- The solution targets privacy-preserving identity workflows for developers and enterprises.
- The article highlights Crescent as a tool to enhance user privacy without sacrificing credential utility.
Context and background
Digital identity systems increasingly balance the need to verify credentials with user privacy. The Crescent library described by Microsoft Research focuses on reducing cross-use tracking while preserving the ability to disclose essential credential information. By combining privacy-aware design with selective disclosure, Crescent aims to support workflows where users can prove attributes without revealing unnecessary data across multiple interactions. This approach aligns with broader trends in privacy-preserving identity technologies that seek to minimize data exposure while maintaining verifiability.
What’s new
Crescent library brings privacy to digital identity systems by introducing mechanisms that prevent tracking across uses and enable selective disclosure of credential data. The library is positioned as a privacy-focused tool for building digital identity experiences where user privacy is a core consideration, rather than an afterthought. The MSR publication presents Crescent as an approach to address privacy concerns inherent in traditional identity workflows while maintaining credential usefulness across applications.
Why it matters (impact for developers/enterprises)
For developers and enterprises building identity platforms, Crescent offers a path to integrate privacy-preserving capabilities directly into credential workflows. By reducing the ability to track users across different services and enabling disclosure of only the necessary credential attributes, Crescent can help organizations address user privacy expectations and potential regulatory considerations without sacrificing the ability to verify credentials.
Technical details or Implementation
The current description of Crescent emphasizes two core capabilities:
- Preventing tracking across uses: the library is designed to minimize cross-service tracing of a single user’s credential interactions.
- Selective disclosure: users can reveal only the portions of their credentials that are strictly necessary for a given verification scenario. Details on specific cryptographic primitives, integration points, or programming interfaces are not provided in the available excerpt. For developers interested in practical integration avenues, the Microsoft Research blog post provides the primary reference and link to learn more.
Key takeaways
- Crescent aims to enhance privacy in digital identity systems by curbing cross-use tracking.
- It supports selective disclosure of credential data to protect user privacy.
- The library targets privacy-preserving identity workflows suitable for modern applications.
- Adoption could help developers and enterprises address privacy expectations while maintaining credential verifiability.
- The primary reference for Crescent is the Microsoft Research blog post.
FAQ
-
What is Crescent library?
Crescent is a library from Microsoft Research designed to enhance privacy in digital identity systems by preventing tracking across uses and enabling selective disclosure of credential data. [source](https://www.microsoft.com/en-us/research/blog/crescent-library-brings-privacy-to-digital-identity-systems/)
-
How does Crescent protect privacy?
It focuses on preventing tracking across uses and allowing users to disclose only the necessary parts of their credentials. [source](https://www.microsoft.com/en-us/research/blog/crescent-library-brings-privacy-to-digital-identity-systems/)
-
Who benefits from Crescent?
Developers and enterprises building digital identity systems, as well as end users who require privacy-preserving credential verification. [source](https://www.microsoft.com/en-us/research/blog/crescent-library-brings-privacy-to-digital-identity-systems/)
-
Where can I learn more?
The Microsoft Research blog post on Crescent provides the primary reference and link to the official information. [source](https://www.microsoft.com/en-us/research/blog/crescent-library-brings-privacy-to-digital-identity-systems/)
References
More news
First look at the Google Home app powered by Gemini
The Verge reports Google is updating the Google Home app to bring Gemini features, including an Ask Home search bar, a redesigned UI, and Gemini-driven controls for the home.
Shadow Leak shows how ChatGPT agents can exfiltrate Gmail data via prompt injection
Security researchers demonstrated a prompt-injection attack called Shadow Leak that leveraged ChatGPT’s Deep Research to covertly extract data from a Gmail inbox. OpenAI patched the flaw; the case highlights risks of agentic AI.
Predict Extreme Weather in Minutes Without a Supercomputer: Huge Ensembles (HENS)
NVIDIA and Berkeley Lab unveil Huge Ensembles (HENS), an open-source AI tool that forecasts low-likelihood, high-impact weather events using 27,000 years of data, with ready-to-run options.
Scaleway Joins Hugging Face Inference Providers for Serverless, Low-Latency Inference
Scaleway is now a supported Inference Provider on the Hugging Face Hub, enabling serverless inference directly on model pages with JS and Python SDKs. Access popular open-weight models and enjoy scalable, low-latency AI workflows.
Google expands Gemini in Chrome with cross-platform rollout and no membership fee
Gemini AI in Chrome gains access to tabs, history, and Google properties, rolling out to Mac and Windows in the US without a fee, and enabling task automation and Workspace integrations.
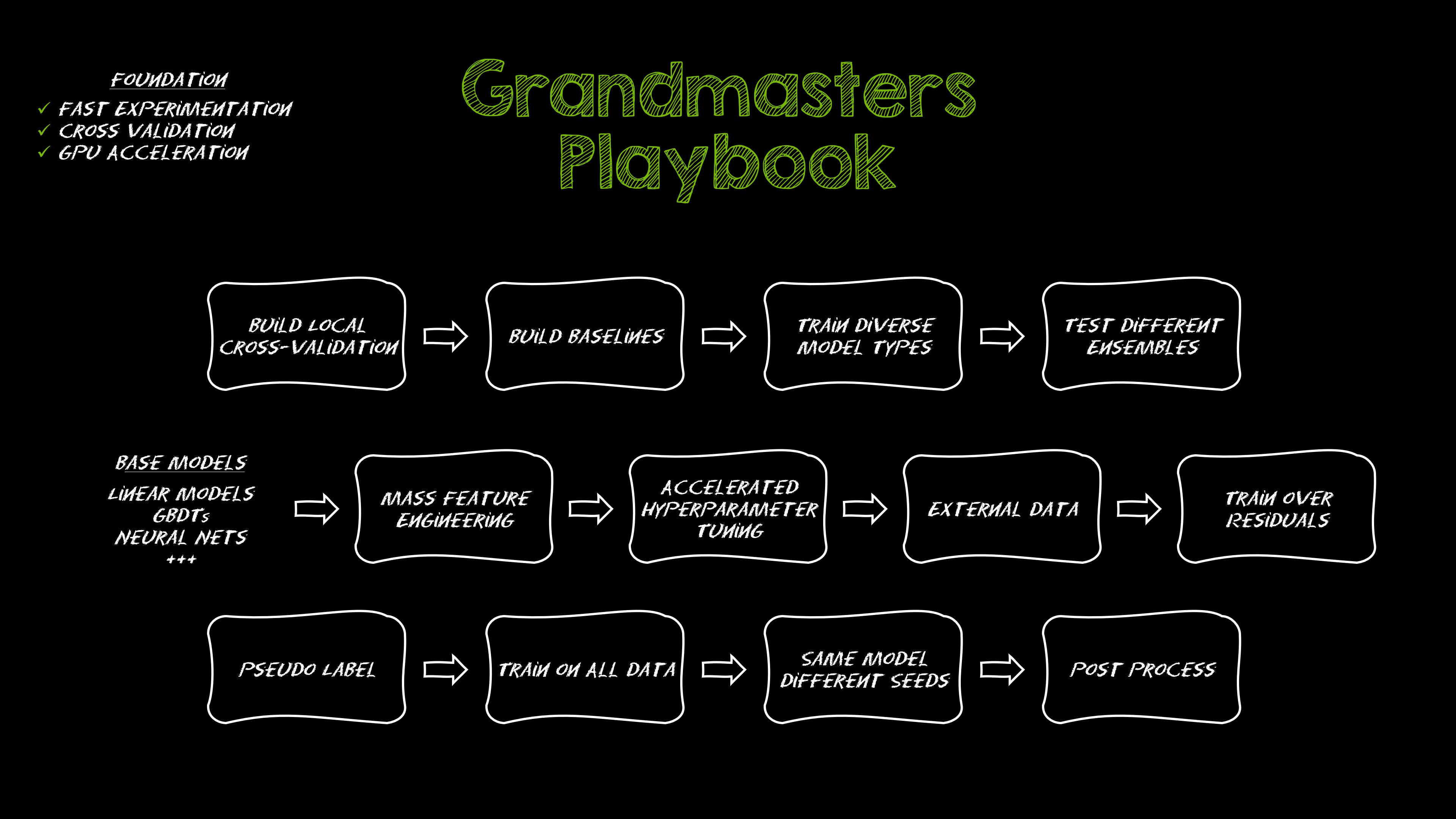
Kaggle Grandmasters Playbook: 7 Battle-Tested Techniques for Tabular Data Modeling
A detailed look at seven battle-tested techniques used by Kaggle Grandmasters to solve large tabular datasets fast with GPU acceleration, from diversified baselines to advanced ensembling and pseudo-labeling.