Improve Data Integrity and Security with Accelerated Hash Functions and Merkle Trees in cuPQC 0.4
TL;DR
- cuPQC SDK v0.4 introduces expanded hash function support and comprehensive Merkle-tree calculations to accelerate data integrity and security tasks on GPUs. Source.
- The release extends cuHash with SHA2, SHA3, SHAKE, and Poseidon2-BabyBear, broadening the set of cryptographic primitives available inside GPU kernels.
- Merkle trees enable verification of data integrity with O(logN) time and support efficient membership proofs and privacy-preserving applications such as zero‑knowledge proofs (ZKPs).
- These additions bolster post-quantum cryptography (PQC) schemes like XMSS, LMS, and SPHINCS+ by providing secure, scalable, and forward‑looking hash-based signatures.
- cuPQC’s design continues to emphasize fused, high‑performance kernels, Link Time Optimization (LTO), and device-side APIs that simplify composing cryptographic circuits inside GPU kernels.
Context and background
As datasets grow, ensuring data security and integrity becomes increasingly important. Cryptographic techniques such as inclusion proofs, data-integrity checks, consistency validation, and digital signatures play a central role in protecting critical workloads. cuPQC is designed to fuse multiple lightweight operations into a single GPU kernel, enabling rapid and efficient cryptographic computations. The SDK features LTO and device-side APIs that help developers implement high-speed cryptographic tasks with fewer kernel launches and lower overhead. The latest release expands on cuPQC v0.3 by adding robust hash function support and Merkle-tree capabilities, broadening the range of applications that can be built on GPU-accelerated cryptography. Source. In this context, Merkle trees provide a scalable mechanism to verify data integrity across large datasets. In a binary Merkle tree, non-leaf nodes are hashes of their two children, while leaves represent the hashes of input data blocks. Once the tree is constructed, proofs for any leaf can be generated and used by verifiers in conjunction with the root hash to validate data integrity. This approach offers substantial efficiency benefits over linear hash chains, particularly when dealing with big data streams or distributed systems. Source. The integration of Merkle trees with accelerated hash functions also supports modern privacy-preserving technologies. When combined with hash-based primitives such as Poseidon, cuPQC enables more efficient constructions for zero-knowledge proofs and other privacy-preserving protocols, aligning with post-quantum security goals. NVIDIA highlights that these capabilities broaden the range of cryptographic applications possible with cuPQC while preserving performance and security.
What’s new
The v0.4 release builds on cuPQC v0.3 by expanding two core areas:
- cuHash: Expanded hash function support now includes SHA2, SHA3, SHAKE, and Poseidon2-BabyBear, enabling a wider set of cryptographic constructions to be fused into GPU kernels. This broadens the toolkit for building fast, secure primitives inside CUDA-enabled workflows. Source.
- Merkle-tree calculations: Comprehensive support for Merkle-tree construction and verification enables efficient data-integrity management and verification processes. Unlike traditional hash chains that require linear time, Merkle trees offer O(logN) time complexity for proofs and verifications. A binary Merkle tree has leaf hashes for input data blocks and internal nodes as hashes of their child nodes. For example, if H_A = Hash(Data A) and H_B = Hash(Data B), then the parent node H_AB = Hash(H_A |H_B). Once the tree is built, proofs can be generated for any leaf and verified against the root hash. This enables precise integrity checks with minimal computational overhead. Source. With Merkle-tree support, cuPQC users gain:
- Faster integrity verification across large datasets via logarithmic proof paths.
- Efficient membership proofs that confirm presence or absence of data elements without exposing entire datasets.
- Stronger foundations for privacy-preserving protocols, including zero-knowledge proofs (ZKPs) that rely on secure hash functions and Merkle-based commitments. The integration leverages specialized hash functions like Poseidon to improve performance and security in ZKP workflows. Source. Post-quantum cryptography (PQC) is another area strengthened by these updates. Hash-based signature schemes such as XMSS, LMS, and SPHINCS+ depend on the structural integrity of Merkle trees and robust hash functions to deliver quantum-resistant signatures. cuPQC’s accelerated primitives support these schemes by enabling faster, GPU-based hashing and tree‑based verification, helping future-proof cryptographic protocols against quantum threats. Source.
Why it matters (impact for developers/enterprises)
- Performance gains: By fusing cryptographic circuits into high-performance GPU kernels and leveraging LTO, cuPQC v0.4 reduces latency and increases throughput for cryptographic tasks, which is crucial for data-intensive workloads such as secure data storage, distributed ledgers, and high-security streaming data.
- Expanded cryptographic repertoire: The expanded cuHash function support allows developers to select the most appropriate hash family for their security and performance requirements, enabling more flexible design choices in both new projects and legacy migrations. Source.
- Robust data integrity verification: Merkle-tree-based proofs provide scalable verification for large datasets with minimal computation, which is highly relevant for systems requiring fast integrity checks, efficient membership proofs, and tamper detection in real time. Source.
- Privacy and security advantages: The combination of hash functions with Merkle-tree support supports privacy-preserving applications and ZKPs, enabling secure verification without disclosing sensitive data. Poseidon-based hashes further optimize performance for privacy-focused protocols. Source.
- Post-quantum readiness: By facilitating PQC schemes that rely on Merkle-tree structures and strong hash functions, cuPQC v0.4 contributes to quantum-resistant signatures and forward-looking cryptographic design. Source.
Technical details or Implementation
cuPQC is designed to fuse various cryptographic circuits into GPU kernels, taking advantage of device-side APIs and Link Time Optimization to minimize kernel launch overhead and maximize throughput. In v0.4, the framework expands two primary pillars:
- cuHash primitives: The new support spans SHA2, SHA3, SHAKE, and Poseidon2-BabyBear. This enables diverse hashing strategies for different security requirements and performance profiles inside cuPQC kernels. Source.
- Merkle-tree calculations: Merkle trees are constructed with leaf hashes representing input data blocks, and parent nodes formed by hashing their child hashes. For a quick recall, if H_A = Hash(Data A) and H_B = Hash(Data B), the parent is H_AB = Hash(H_A |H_B). The path from a leaf to the root consists of sibling hashes at each level, forming the proof required to reconstruct the root and verify membership. This yields a logarithmic proof path length, enabling rapid verification even as datasets scale. Source. To illustrate the flow, consider generating a Merkle-proof for a leaf like H_E = Hash(Data E): the proof sequence includes the necessary siblings at each level, such as [H_F, H_GH, H_ABCD], which the verifier uses along with the known root hash to recompute and compare the root. If the recomputed root matches the known root, the proof is valid. This process demonstrates how Merkle trees provide efficient, scalable data integrity verification. Source. Combined, these enhancements enable a broad set of cryptographic workflows on GPUs, including:
- Hash-based signatures in PQC schemes (XMSS, LMS, SPHINCS+) that rely on Merkle-tree structures and robust hash functions.
- ZKP-based protocols that benefit from fast, private verifications without revealing the underlying data. The Poseidon family has been highlighted as a hash function optimized for both performance and security in privacy-preserving systems within cuPQC v0.4. Source. If you’re ready to explore, you can download cuPQC and start integrating its GPU-accelerated primitives into your projects. The release notes and comprehensive documentation offer guides, API references, and troubleshooting tips to help you leverage these features effectively. Source.
Key takeaways
- cuPQC v0.4 extends cryptographic capabilities on GPUs with expanded cuHash support and full Merkle-tree calculations.
- Hash families now include SHA2, SHA3, SHAKE, and Poseidon2-BabyBear, broadening cryptographic options inside kernels.
- Merkle trees enable O(logN) proofs and efficient membership verification for large datasets, boosting scalability.
- The combination supports privacy-preserving and post-quantum cryptography workflows, including ZKPs and PQC schemes.
- The architecture continues to emphasize fused, high-performance kernels, LTO, and device-side APIs for easier composition of cryptographic circuits in GPU code.
FAQ
-
What is cuPQC v0.4 primarily adding?
It adds expanded hash function support (SHA2, SHA3, SHAKE, Poseidon2-BabyBear) and comprehensive Merkle-tree calculations for efficient data integrity verification on GPUs.
-
How do Merkle trees improve verification efficiency?
Merkle trees reduce verification complexity from linear to logarithmic (O(logN)) by using a path of sibling hashes from a leaf to the root to prove data integrity.
-
What applications benefit from these features?
Privacy-preserving protocols like zero-knowledge proofs, hash-based post-quantum signatures (XMSS, LMS, SPHINCS+), and general data-integrity verification in large datasets.
-
How should I start using cuPQC v0.4?
Download cuPQC and refer to the comprehensive documentation, API references, and usage examples to begin integrating the primitives into your GPU kernels. [Source](https://developer.nvidia.com/blog/improve-data-integrity-and-security-with-accelerated-hash-functions-and-merkle-trees-in-cupqc-0-4/).
References
More news
NVIDIA HGX B200 Reduces Embodied Carbon Emissions Intensity
NVIDIA HGX B200 lowers embodied carbon intensity by 24% vs. HGX H100, while delivering higher AI performance and energy efficiency. This article reviews the PCF-backed improvements, new hardware features, and implications for developers and enterprises.
OpenAI reportedly developing smart speaker, glasses, voice recorder, and pin with Jony Ive
OpenAI is reportedly exploring a family of AI devices with Apple's former design chief Jony Ive, including a screen-free smart speaker, smart glasses, a voice recorder, and a wearable pin, with release targeted for late 2026 or early 2027. The Information cites sources with direct knowledge.
Shadow Leak shows how ChatGPT agents can exfiltrate Gmail data via prompt injection
Security researchers demonstrated a prompt-injection attack called Shadow Leak that leveraged ChatGPT’s Deep Research to covertly extract data from a Gmail inbox. OpenAI patched the flaw; the case highlights risks of agentic AI.
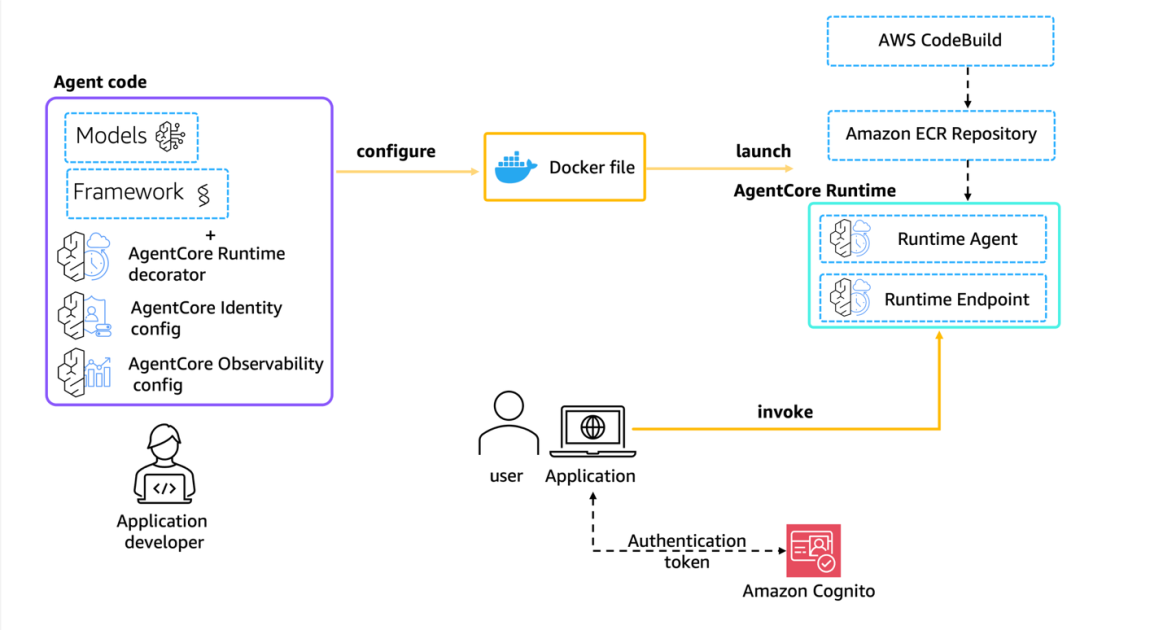
Move AI agents from proof of concept to production with Amazon Bedrock AgentCore
A detailed look at how Amazon Bedrock AgentCore helps transition agent-based AI applications from experimental proof of concept to enterprise-grade production systems, preserving security, memory, observability, and scalable tool management.
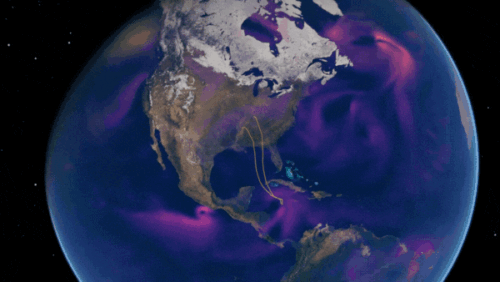
Predict Extreme Weather in Minutes Without a Supercomputer: Huge Ensembles (HENS)
NVIDIA and Berkeley Lab unveil Huge Ensembles (HENS), an open-source AI tool that forecasts low-likelihood, high-impact weather events using 27,000 years of data, with ready-to-run options.
How chatbots and their makers are enabling AI psychosis
Explores AI psychosis, teen safety, and legal concerns as chatbots proliferate, based on Kashmir Hill's reporting for The Verge.