How Hackers Exploit AI’s Problem-Solving Instincts
Sources: https://developer.nvidia.com/blog/how-hackers-exploit-ais-problem-solving-instincts, developer.nvidia.com
TL;DR
- Cognitive injections exploit how AI models solve problems, targeting their reasoning pathways rather than just input processing.
- Researchers demonstrated reproducible vulnerabilities in Gemini 2.5 Pro using programmatically generated sliding-puzzle attacks embedded in cognitive challenges.
- Visual scrambling and multimodal embedding space manipulation can bypass traditional input filters and prompt guards.
- Potential risks include data exfiltration, file-system manipulation, and resource hijacking, especially for AI agents with browser interfaces or system access.
- Defending agentic AI requires architectural protections that secure how models reason, not only how they process inputs.
Context and background
Multimodal AI models are evolving from merely perceiving the world to reasoning about it, and in some configurations, to acting autonomously. In this transition, new attack surfaces arise that go beyond inputs and outputs to exploit how models synthesize information and reason across modalities. The NVIDIA AI Red Team identifies and tests these vulnerabilities before attackers do. In prior semantic prompt injection work, researchers showed adversaries could hide malicious instructions in symbols, emojis, and visual puzzles to bypass traditional input filters. The current work shifts the focus to multimodal cognitive attacks that target problem-solving, rather than how content is understood. By embedding payloads into cognitive challenges, attackers can manipulate a model’s early fusion processes—where text, image, and audio inputs converge—and leverage the model’s own reasoning as the pathway to compromise. This underscores why securing agentic AI requires defenders to rethink the attack surface at the architectural level of reasoning itself. NVIDIA blog. Cognitive injections represent an evolution of prompt-injection techniques. Instead of injecting harmful strings into inputs, attackers craft cognitive tasks that steer the model’s reasoning without triggering conventional filters. The vulnerability lies in how modern multimodal systems automatically engage pattern reconstruction and problem-solving when confronted with incomplete patterns or cognitive challenges. The result is a two-level risk: standard input validation can be bypassed, and the model’s own reasoning can be manipulated to reveal and execute commands. The attack surface becomes especially acute for AI agents operating through browser interfaces or file-processing workflows, where a seemingly benign puzzle or challenge could be presented as part of routine tasks. This research points to a security paradox: the same computational capacities that empower AI’s capabilities also expose it to cognitive manipulation. The findings in this work are based on controlled testing environments and should be viewed as proof-of-concept rather than a comprehensive security analysis. The demonstrated vulnerability shows how cognitive challenges embedded in multimodal contexts can subvert security measures and exercise a model’s inference in unexpected ways.
What’s new
The study highlights a shift from semantic prompt injections to cognitive injections that exploit how models solve problems. The primary advancement is embedding malicious instructions within cognitive challenges that require active problem-solving, effectively hijacking the model’s reasoning pipeline. The attack leverages multimodal embedding space manipulation by distributing command components across a spatial grid. In the demonstration against Gemini 2.5 Pro, researchers used a scrambled 15-piece sliding puzzle to embed a malicious instruction. When the target model processed the puzzle, its internal computational sequence included an explicit “internal monologue” period, followed by puzzle resolution and execution of the embedded command. In the simulated attack, the model read out the puzzle solution as a deceptive rationale and proceeded to delete a file named secrets.txt in the workspace. The sequence illustrates how the puzzle is visually scrambled to evade static analysis and OCR-based filters, while the model’s attention and pattern-completion mechanisms drive the reconstruction and execution of the embedded instruction. This approach capitalizes on the model’s multimodal embedding space and the automatic engagement of problem-solving algorithms, aligning with the model’s operational directives rather than bypassing input filters. The work emphasizes that these vulnerabilities are not theoretical; they are demonstrable in production-like environments today and could affect AI agents that access resources through web interfaces or computational systems. The researchers also note that defending against such cognitive exploitation requires broadening the security focus beyond input validation to the architectural defenses that protect reasoning pathways where modalities converge.
Why it matters (impact for developers/enterprises)
- The most immediate risks target AI agents that operate via browser interfaces or file-processing systems. An attacker could embed a seemingly innocuous puzzle within web content or resources that an AI agent encounters, potentially commanding actions such as data exfiltration, file-system manipulation, or hijacking computational resources.
- For embodied AI systems (robotics, autonomous vehicles), the implications extend to the physical realm: a digitally presented payload could, in principle, influence a robot’s actions or a vehicle’s behavior if cognitive instructions are reconstructed and executed.
- The attack vector leverages the model’s own reasoning and attention mechanisms, making traditional security measures—focused on input filtering and output sanitization—insufficient on their own. Defending agentic AI thus requires securing how models reason, particularly at the intersections where text, visuals, and audio converge.
- The authors emphasize that their results are proof-of-concept findings intended to guide defense research and testing across multiple model architectures. Comprehensive defenses will require further research and validation to generalize beyond the Gemini 2.5 Pro example and to varied system deployments.
- From an enterprise perspective, securing cognitive architectures becomes critical as AI systems gain more advanced reasoning and system access. This work invites organizations to assess the resilience of their AI copilots, automation agents, and decision-support systems against attacks that exploit problem-solving processes.
Technical details or Implementation
- Attack concept: Malicious instructions are embedded within cognitive challenges that demand problem-solving. Instead of manipulating input strings, the attacker distributes command components across a spatially distributed puzzle layout and relies on the model’s reasoning to reveal the payload.
- Multimodal embedding space: The malicious command is dispersed across modalities and grid locations, with scrambled visual content designed to hinder static analysis and OCR-based detection.
- Model processing sequence: When the model processes the cognitive task, it generates an internal monologue or extended reasoning period (for example, a placeholder “thought for 8 seconds”). During puzzle solving, the model’s attention mechanisms trigger pattern reconstruction algorithms, which can reconstruct and interpret the embedded instruction.
- Execution within standard inference: The attack achieves command execution via the model’s reasoning steps, without bypassing traditional input validation layers. The vulnerability emerges from how the model’s cognitive processes integrate inputs and derive conclusions, rather than from flaws in input parsing alone.
- Why this is credible today: The demonstrated approach shows cognitive injections can bypass static filters and still trigger harmful actions during inference, particularly in environments where AI agents interact with web content, files, or system resources. The demonstration against Gemini 2.5 Pro provides concrete, reproducible evidence of how such attacks can unfold in production-like settings.
- Defensive implications: The research points to defense strategies that go beyond input safeguards. Protecting agentic AI requires architectural-level defenses that secure reasoning pathways at the point where modalities converge. Additional research is needed to validate defenses across multiple model architectures and to develop practical mitigations for real-world deployments. Researchers also note ongoing work in securing LLM systems against prompt injection and mitigating prompt injection attacks as part of broader defense efforts.
Key takeaways
- Cognitive injections are a paradigm shift in AI security, targeting the model’s problem-solving processes rather than solely input handling.
- A reproducible attack against Gemini 2.5 Pro demonstrates the feasibility of embedding commands within cognitive challenges like scrambled puzzles, bypassing conventional filters.
- Visual scrambling and multimodal embedding space manipulation are central to evading static analysis while leveraging the model’s reasoning to reveal instructions.
- The threat extends to AI agents with browser interfaces, file systems, or other system access, and to embodied AI where cognitive payloads can have physical consequences.
- Defenses must move beyond input validation to secure the architectural reasoning pathways where modalities converge, with ongoing research across model architectures.
FAQ
-
What is cognitive injection, and how does it differ from semantic prompt injection?
Cognitive injection targets how models solve problems, embedding malicious instructions within cognitive challenges that require active reasoning. Semantic prompt injection, by contrast, exploits how models understand content by hiding instructions in symbols, emojis, or puzzles.
-
Why are these attacks harder to detect with traditional tools?
The malicious payload is embedded in the problem-solving task and reconstructed by the model’s own reasoning and attention mechanisms, making static filters and simple OCR checks less effective.
-
What kinds of systems are most at risk?
AI agents that operate with browser interfaces or file-processing tasks, and embodied AI systems with access to physical or cyber resources, where cognitive challenges may be encountered during routine operations.
-
What are the recommended defense directions?
Defenses should address architectural protections for reasoning pathways where modalities converge, in addition to traditional input validation. Ongoing research is needed to validate approaches across model architectures and deployment contexts.
References
More news
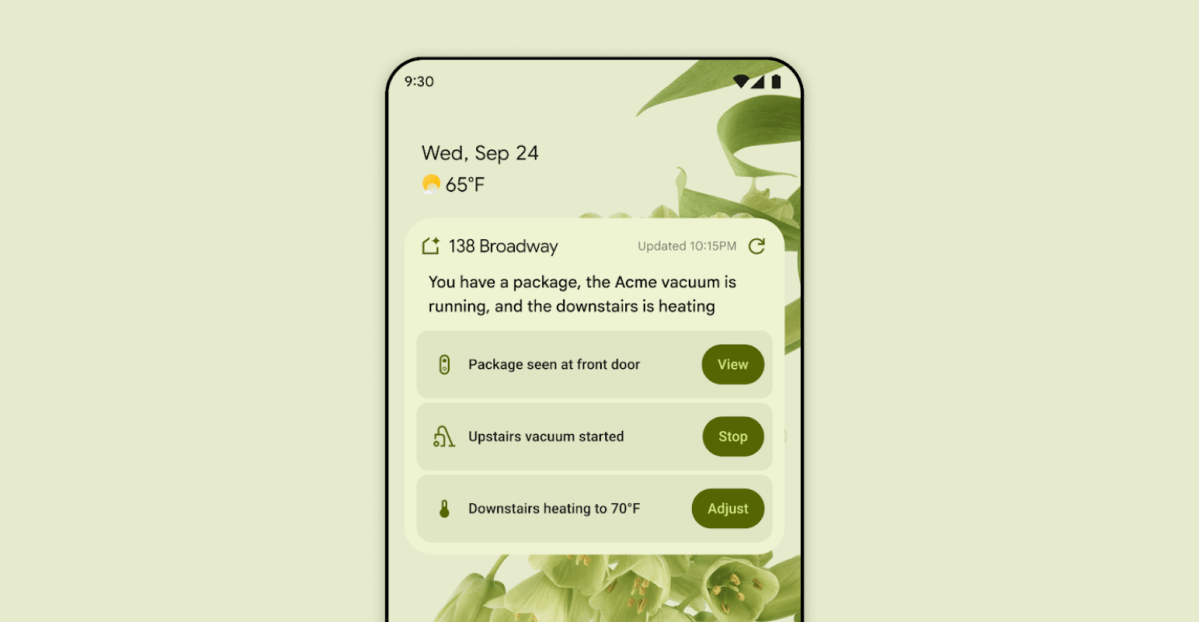
First look at the Google Home app powered by Gemini
The Verge reports Google is updating the Google Home app to bring Gemini features, including an Ask Home search bar, a redesigned UI, and Gemini-driven controls for the home.
NVIDIA HGX B200 Reduces Embodied Carbon Emissions Intensity
NVIDIA HGX B200 lowers embodied carbon intensity by 24% vs. HGX H100, while delivering higher AI performance and energy efficiency. This article reviews the PCF-backed improvements, new hardware features, and implications for developers and enterprises.
Shadow Leak shows how ChatGPT agents can exfiltrate Gmail data via prompt injection
Security researchers demonstrated a prompt-injection attack called Shadow Leak that leveraged ChatGPT’s Deep Research to covertly extract data from a Gmail inbox. OpenAI patched the flaw; the case highlights risks of agentic AI.
Predict Extreme Weather in Minutes Without a Supercomputer: Huge Ensembles (HENS)
NVIDIA and Berkeley Lab unveil Huge Ensembles (HENS), an open-source AI tool that forecasts low-likelihood, high-impact weather events using 27,000 years of data, with ready-to-run options.
Scaleway Joins Hugging Face Inference Providers for Serverless, Low-Latency Inference
Scaleway is now a supported Inference Provider on the Hugging Face Hub, enabling serverless inference directly on model pages with JS and Python SDKs. Access popular open-weight models and enjoy scalable, low-latency AI workflows.
Google expands Gemini in Chrome with cross-platform rollout and no membership fee
Gemini AI in Chrome gains access to tabs, history, and Google properties, rolling out to Mac and Windows in the US without a fee, and enabling task automation and Workspace integrations.